John Robb on the evolution of cyberwar
From super-empowered employees and rogue traders to "managed perception"
The concept of cyberwar has gone from science fiction to science fact in a few decades. Since the threat of a cyberwar was introduced for the masses on the cover of Time magazine in 1995, much has changed.
Alvin Toffler described the concept of third generation war in “War and Anti-War” in 1983, a few decades later a fourth and fifth generation had emerged. As war moved from the physical to the digital, boundaries of conflicts blurred - causing massive headaches and frustration in the security industry.
The Plausible Futures Newsletter had the opportunity to have a talk with John Robb, a veteran in the field of counterterrorism and a legend in the realm of future warfare.
– To a large extent my devotion to the military was inevitable. My family, if there is such a thing, is military caste. My father was a fighter pilot, one uncle was in the Army and another a Navy pilot who was shot down in Vietnam and escaped. My father-in-law is a B-52 navigator and I have two brothers in the AF and NSA, a brother-in-law working with the F-16, a cousin working as a Marine F-18 pilot and a sister and a sister-in-law working as AF nurses, Robb transmit encrypted from his high-tech bunker somewhere in the US.
– What really got me started was reading military history on my own. I grew up playing war games after I bought a dozen used Avalon Hill games for a dollar at a tag sale - how lucky is that?
In 2004, Robb began the blog Global Guerrillas to cover developments in terrorism and guerrilla warfare. In April 2007, he published Brave New War, introducing the concept of open-source warfare and super-empowered terrorism. His current Global Guerrillas Report can be found on Patreon.
From a cancelled career in space to counterterrorism
Despite his initial military interest, Robb got into the space race.
– I went to the AF Academy, where my two brothers followed me, because it had an Astronautical Engineering program and was the best way to get into pilot training. I got my Astro degree and got through pilot training only to see the US space programme shut-down due to a shuttle explosion. At that point, I changed direction and went into special operations tier one counterterrorism.
What got you into cybersecurity and how has the field evolved since your first experiences?
– I never formally entered the field of cybersecurity. It's more that I fell into it due to a combination of building a couple of global technology companies and writing a book about how warfare and terrorism were evolving. It's evolving pretty much as expected.
Attacks on infrastructure
Considering the recent attack on Colonial pipeline and many others – how vulnerable are western infrastructure to such attacks?
– Very. However, from the reports, the Colonial pipeline shut itself down because it lost its ability to bill customers. Shutting down the pipeline because of that is poor management.
– However, in general, companies, organizations and individuals across the US and EU are being attacked routinely. Although it isn't possible to stop all of this, it is possible to achieve some level of deterrence for the most important systems. Something I proposed in a couple of DoD strategy sessions a decade ago, which was ignored.
– My approach is to recognize that not every system is critical. Also, we need to clearly delineate those systems that are critical, like infrastructure, healthcare, and other essential services. We also need to classify any attack on these critical systems as an act of terrorism. Depending on the severity there should be a proportionate response in the form of sanctions, counterattacks, disconnection from the Internet against states that support these attacks, and lethal consequences for the actors.
– Members of ransomware platforms could find their faces on playing cards with a bounty attached, as we saw in Iraq.
New technology and threats
Robb has a keen interest in technology as a driving force in modern warfare.
– I consider the crypto ecosystem both an opportunity and a threat. Now it's mostly at the proof-of-concept stage, like the early Internet companies that had traffic without revenue. Eventually, the blockchain industry will find a way to generate revenue to justify their valuations, but they will do this at the expense of the existing financial services.
Any threats?
– Unfortunately, the pandemic has made things worse because we are more reliant on online infrastructure than ever, and the dark net has become the critical infrastructure for international terrorism and crime.
Drawing a red line between black and white hat hacking
Considering Wikileaks, Snowden, the Panama-papers and other “ethical” hackers - where do you draw the line between white and black hat?
– I'm OK with the occasional data leak. It serves a good purpose: it lets people know that if they do something bad and there is a digital trail, it could end up in the public domain. The biggest harm it does is how it impacts organizations.
– The reason Snowden was able to steal so much data is that the systems were organized to break down silos, super-empower employees, and encourage cross-domain synergy in a post 9/11-environment. This was done to detect the next threat early enough and be able to do something about it. Snowden, as a super-empowered employee, abused his position and forced everyone back into silos, Robb says.
– That's a big paradox in modern organizations. Everyone wants super-empowered employees that can fully leverage the tools and information the organization provide, but the same organization can also become vulnerable because of these super-employees. Think how rogue traders at big banks can drive them into bankruptcy, he says and add:
– It's interesting to note that some of the most disruptive events caused by hackers have been data leaks rather than attacks on infrastructure.
NATO Article 5 and proportionate sanctions
How should states respond to other state sponsored cyberattacks considering NATO Article 5?
– There are three different categories of attacks. The vast majority and most common is criminal attacks by non-state groups, state-sanctioned or not. I've detailed how to draw this red line above. The second category is probes and espionage that resembles the cold war state vs. state situation where everyone just plays the game. This is still common.
– The third category consist of state-sponsored attacks on infrastructure. In my view this is the only thing that would trigger Article 5 in NATO. These types of attacks are uncommon and should be classified as an act of war, Robb says.
Social AIs and “managed perception”
What emerging threats do you consider having great the greatest damage potential?
– I'm not that worried about disruptions by hackers, we can handle them. I am worried about how the social AIs, that billions of people are feeding data and billions of dollars a month are spent building, can be used for repression in the future. A system that can actively manage information flows down to the individual level through “managed perceptions” and “nudge ideas” have a scary potential for damage.
How could mega-corporation and their quasi-monopolies become a threat concerning security, censorship, and politics?
– It doesn't look good. In the US, corporations are in control. They showed that when they disconnected a sitting US president and millions of his supporters from social media platforms. The EU is trying to follow an “ostrich strategy” and wait this out, but it won't work. Meanwhile China has taken control of its corporations and is actively aligning them under a fascist organizational model, he says.
Physical defense
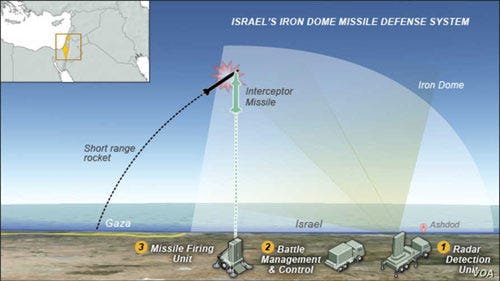
The Israeli Iron Dome has proven efficient with an over 80 percent success rate in Israel these last days. How could defense technology and measures like missile defense change warfare?
– Point air defense solutions like Iron Dome work great in small areas, but are expensive to set up and maintain. Despite that, it worked for Israel and kept them safe. However, their aggressive bombing campaign has made them vulnerable to online attacks via social media. I call this “being Trumpified”.
Sources of inspiration
What living or dead thinker, philosopher, futurist, or scientist would you like to spend a weekend with – and what would you talk about?
– Nietzsche, HG Wells, George Orwell and Max Weber. I'd love to see how their minds bounce off of where we are today, Robb concludes.